Explain Flood Ping
Explain Flood Ping, Indeed recently has been hunted by consumers around us, perhaps one of you personally. People now are accustomed to using the internet in gadgets to view video and image information for inspiration, and according to the name of this article I will discuss about
If the posting of this site is beneficial to our suport by spreading article posts of this site to social media marketing accounts which you have such as for example Facebook, Instagram and others or can also bookmark this blog page.
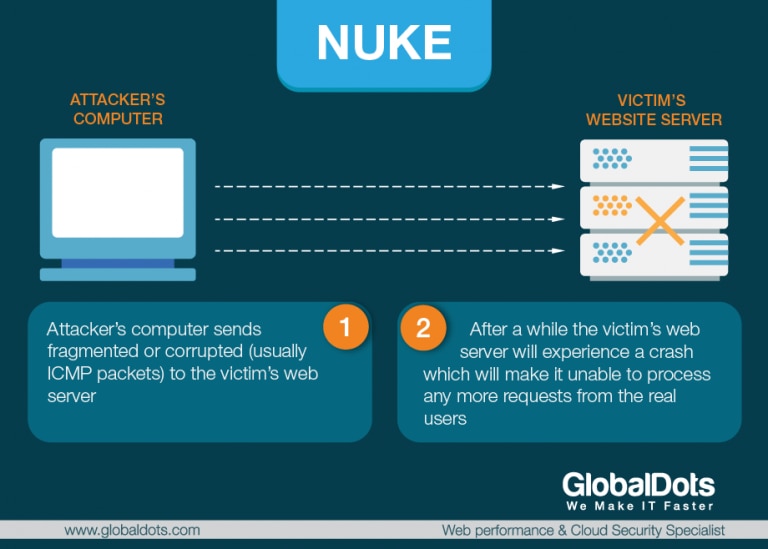
Icmp ping flood similar in principle to the udp flood attack an icmp flood overwhelms the target resource with icmp echo request ping packets generally sending packets as fast as possible without waiting for replies.

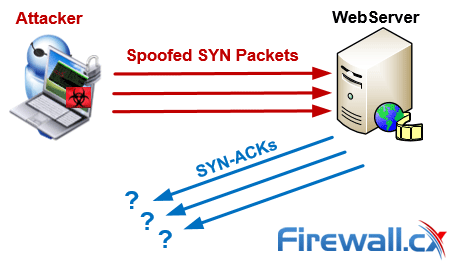
Question mark exclamation mark or full stop. In the syn flood attack the sender sends to the target many syn packets from ips which are not on line or never answer to the syn ack packets sent back from the target to the attacker in such way the target tcpip stack is exhausted due to only two way opened connections that will never fully accomplished. A denial of service attack can be carried out using syn flooding ping of death teardrop. A router disclosed ping flood targets routers in order to disrupt communications between computers on a network.
Router disclosed here a ping flood targets routers with the objective of interrupting communications between computers on a network. Targeted local disclosed in this type of attack a ping flood targets a specific computer on a local network. There are two types of attacks denial of service and distributed denial of service.
An attacker needs to have physical. Flood the network super users can send hundred or more packets per second using f option. The 3rd way of the tree way handshake will never happen.
A ping flood is a simple denial of service attack where the attacker overwhelms the victim with icmp echo request packetsthis is most effective by using the flood option of ping which sends icmp packets as fast as possible without waiting for replies. W e often use the cmd command ping to mostly check if a server or a gateway is up and. It prints a when a packet is sent and a backspace is printed when a packet is received.
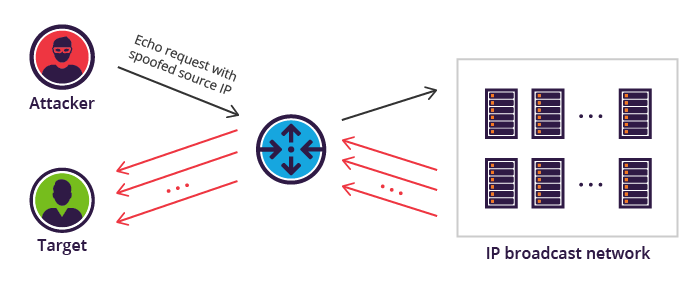
A ping flood is a denial of service attack in which the attacker attempts to overwhelm a targeted device with icmp echo request packets causing the target to become inaccessible to normal traffic. In this case the attacker must obtain the ip address of the destination beforehand. A blind ping flood involves using an.
Most implementations of ping require the user to be privileged in order to specify the flood option. When the attack traffic comes from multiple devices the attack becomes a ddos or distributed denial of service attack. Attack description a targeted local disclosed ping flood targets a single computer on a local network.
A continuous ping will cause buffer overflow at the target system and will cause the target system to crash. Flooding is used in bridging and in systems such as usenet and peer to peer file sharing and as part of some routing protocols including ospf dvmrp and those used in ad hoc wireless networks.